Understanding Information Security and Risk Management
Developing an information security and risk management strategy – Information security and risk management are critical components of any organization’s cybersecurity strategy. Information security focuses on protecting the confidentiality, integrity, and availability of data, while risk management helps organizations identify, assess, and mitigate risks to their information assets.
Developing an information security and risk management strategy is crucial for organizations facing the challenges of management in an organization, such as aligning goals , managing resources , and motivating employees. By integrating security measures into the organization’s overall strategy, businesses can mitigate risks, protect sensitive data, and maintain compliance with industry regulations.
Developing a comprehensive information security and risk management strategy is essential for protecting an organization’s data and ensuring its business continuity. An effective strategy can help organizations reduce the likelihood of security breaches, comply with regulatory requirements, and build trust with customers and partners.
Developing an information security and risk management strategy is essential for protecting sensitive data and ensuring business continuity. Effective strategies involve identifying and assessing risks, implementing controls to mitigate them, and monitoring the environment for potential threats. In healthcare settings, clorpactin is an effective agent for managing bioburden because it reduces the risk of infection and contamination.
A comprehensive information security and risk management strategy can help organizations protect their assets and maintain compliance with regulatory requirements.
Key Components of an Information Security and Risk Management Strategy
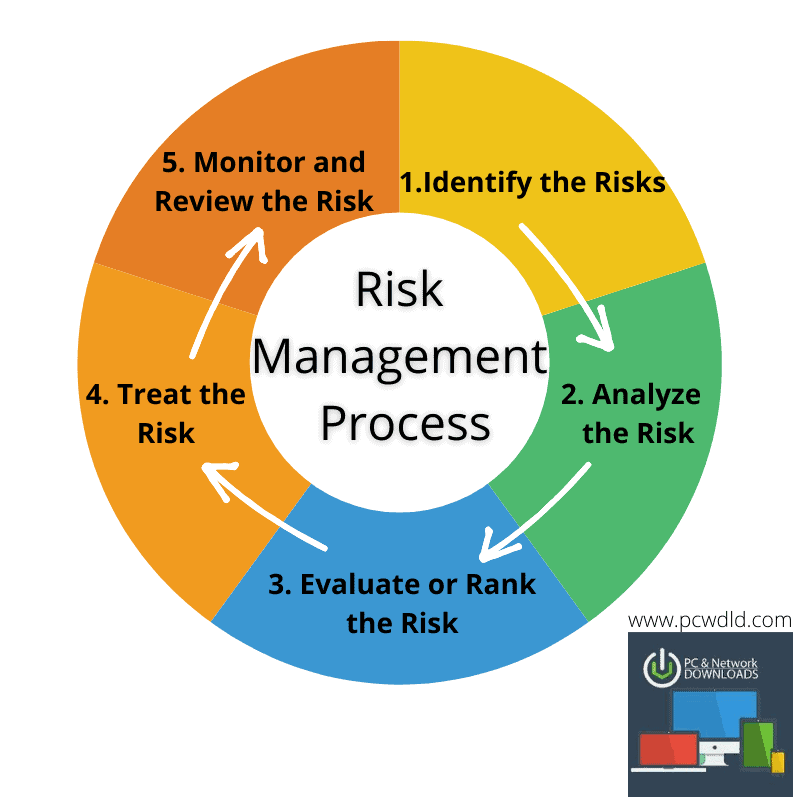
An effective information security and risk management strategy should include the following key components:
- Risk assessment: Identifying and assessing the risks to information assets
- Security controls: Implementing measures to mitigate the identified risks
- Incident response plan: Establishing a plan for responding to security breaches
- Business continuity plan: Ensuring the organization can continue to operate in the event of a security breach
- Governance and oversight: Establishing clear roles and responsibilities for information security and risk management
Developing a Risk Management Framework
A risk management framework provides a structured approach to identifying, assessing, and mitigating risks. There are several different risk management frameworks available, including the ISO 31000 Risk Management Standard and the NIST Cybersecurity Framework.
Developing an information security and risk management strategy requires a comprehensive understanding of cross-cultural management, as outlined in the Cross-Cultural Management: An International Journal. This journal explores the impact of cultural differences on organizational behavior, providing insights that can enhance the effectiveness of information security measures across diverse global teams.
When selecting a risk management framework, organizations should consider their industry, size, and risk appetite. It is important to choose a framework that is aligned with the organization’s business objectives and provides a comprehensive approach to risk management.
Developing an information security and risk management strategy requires a comprehensive approach that includes establishing a robust diary management system. As described in an effective diary management system , maintaining accurate and detailed records of security events, vulnerabilities, and risk assessments is crucial for identifying and mitigating potential threats.
This system serves as a valuable tool for developing and implementing effective security measures, ensuring compliance with regulations, and facilitating continuous improvement efforts within the information security and risk management strategy.
Identifying and Assessing Risks
The first step in developing an information security and risk management strategy is to identify and assess the risks to information assets. This can be done using a variety of methods, including risk assessment tools and techniques.
Developing an information security and risk management strategy is crucial for safeguarding an organization’s data and assets. This involves establishing policies and procedures to mitigate potential threats. However, it’s important to remember that a manager’s approach in enforcing these policies should be professional and respectful.
As discussed in this article , shouting at employees can create a hostile work environment and undermine morale. Instead, managers should focus on open communication, constructive criticism, and positive reinforcement to promote a productive and secure workplace.
When identifying risks, it is important to consider both internal and external threats. Internal threats include malicious insiders, human error, and system failures. External threats include cyberattacks, natural disasters, and supply chain disruptions.
Developing an information security and risk management strategy requires managers to be assertive in their decision-making and communication. This includes being able to clearly articulate the risks and benefits of various security measures, as well as being able to persuade others to support their decisions.
For more on the characteristics of an assertive manager , refer to the link provided. Assertiveness is essential for developing and implementing an effective information security and risk management strategy that protects an organization’s data and systems.
Developing Security Controls
Once the risks have been identified and assessed, the next step is to develop security controls to mitigate the risks. Security controls can be either technical or non-technical.
Developing an information security and risk management strategy is crucial for organizations to protect their sensitive data and assets. However, conflicts within an organization can hinder effective implementation. Conflict management in an organization involves identifying and resolving disputes to maintain a harmonious work environment.
By addressing conflicts effectively, organizations can foster collaboration, reduce stress, and enhance productivity, ultimately contributing to a more robust information security and risk management strategy.
- Technical controls include firewalls, intrusion detection systems, and encryption.
- Non-technical controls include policies, procedures, and training.
When selecting security controls, it is important to consider the cost, effectiveness, and ease of implementation.
Implementing and Monitoring the Strategy, Developing an information security and risk management strategy
Once the information security and risk management strategy has been developed, it is important to implement and monitor the strategy. The strategy should be implemented in a phased approach, with each phase being tested and evaluated before moving on to the next phase.
The strategy should also be monitored on an ongoing basis to ensure that it is effective and that it is being followed. The monitoring process should include regular reviews of the risk assessment, security controls, and incident response plan.
Developing an information security and risk management strategy is crucial for businesses of all sizes. It involves identifying, assessing, and mitigating risks to protect sensitive data and assets. One key aspect of this strategy is managing access to online advertising platforms like Facebook.
To effectively create and manage ad campaigns, it is essential to create an ad account in Facebook Business Manager. This account provides a central hub for managing multiple ad accounts, tracking campaign performance, and ensuring compliance with advertising regulations.
By integrating this step into your information security and risk management strategy, you can enhance the security and effectiveness of your online advertising efforts.
Continuous Improvement
Information security and risk management is an ongoing process. The strategy should be reviewed and updated on a regular basis to ensure that it is aligned with the organization’s changing business needs and risk landscape.
Continuous improvement is essential for maintaining an effective information security and risk management strategy. Organizations should regularly review their strategy and make changes as needed to improve its effectiveness.
Last Word
Implementing a robust information security and risk management strategy is not a one-time endeavor; it requires continuous monitoring, evaluation, and improvement. By embracing a proactive approach, organizations can stay ahead of evolving threats and maintain a secure environment for their operations.
FAQ Resource: Developing An Information Security And Risk Management Strategy
What is the purpose of an information security and risk management strategy?
An information security and risk management strategy provides a framework for organizations to protect their critical information assets, mitigate risks, and maintain regulatory compliance.
What are the key components of an information security and risk management strategy?
The key components include identifying and assessing risks, developing security controls, implementing and monitoring the strategy, and continuous improvement.
How can organizations identify and assess risks to information security?
Organizations can identify and assess risks through vulnerability assessments, threat intelligence, and risk analysis techniques.
What are the different types of security controls?
Security controls can be classified into preventive, detective, and corrective controls, each serving a specific purpose in protecting information assets.
Why is continuous improvement important in information security and risk management?
Continuous improvement is essential to address evolving threats, maintain regulatory compliance, and enhance the overall effectiveness of the information security program.