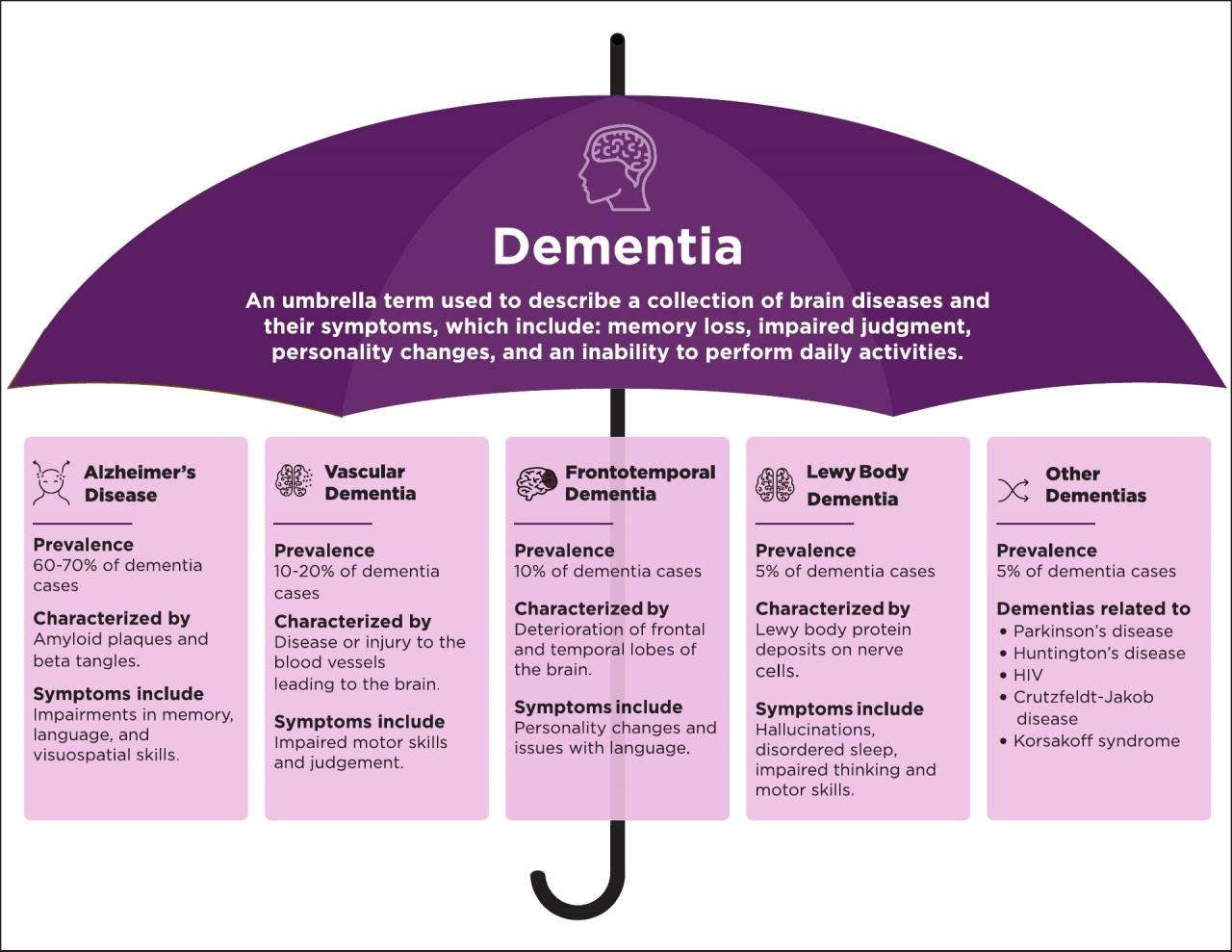
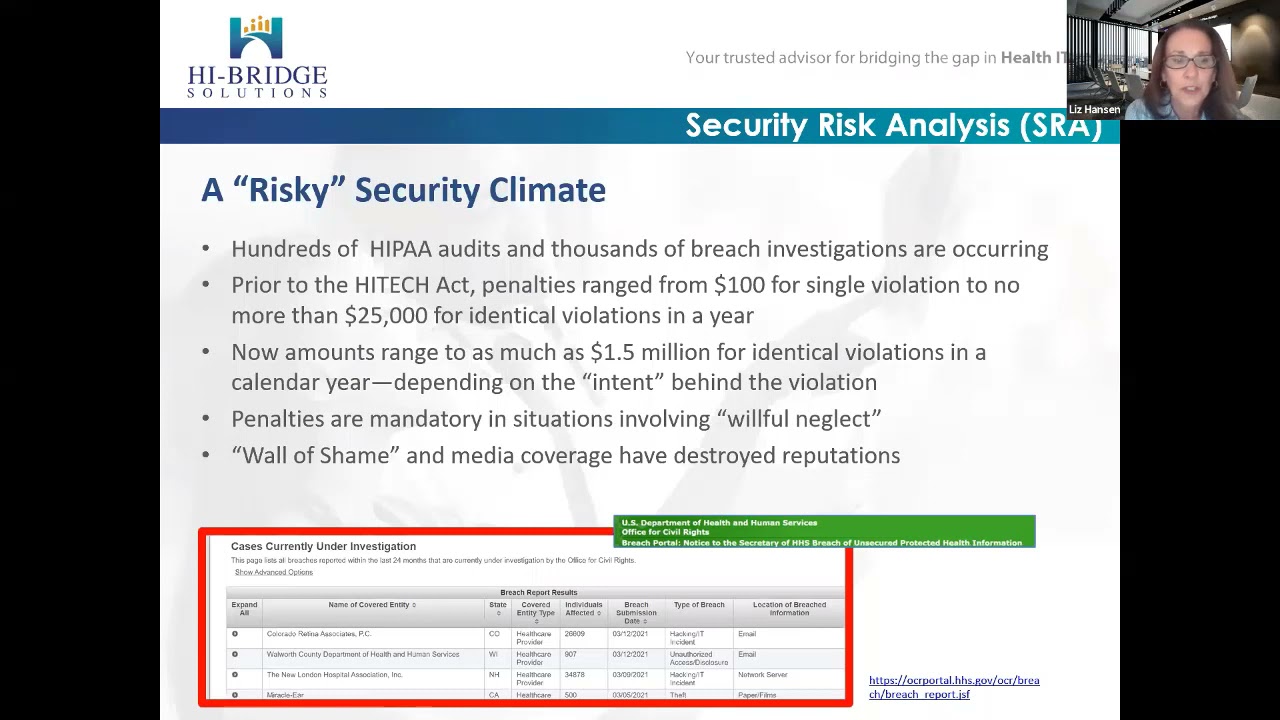
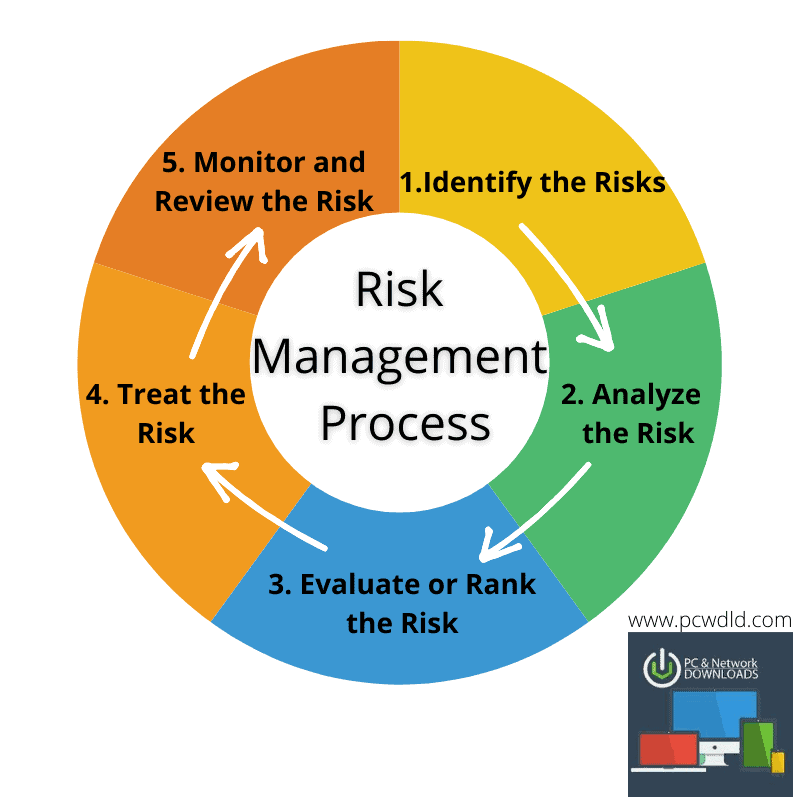
Isabella: An IT Security Sentinel for a State Agency
Isabella’s Role as an IT Security Manager Isabella is an it security manager for a state agency – As an IT Security Manager for a state agency, Isabella plays a critical role in safeguarding the agency’s IT systems and data from cyber threats. Her primary responsibilities include: Developing and implementing cybersecurity policies and procedures Conducting … Read more