A company stores confidential data in an amazon aurora postgresql – Storing confidential data in the cloud requires robust security measures. Amazon Aurora PostgreSQL offers a range of features to protect sensitive information, ensuring compliance and peace of mind.
In this comprehensive guide, we’ll explore the best practices, encryption options, access control mechanisms, and monitoring capabilities of Aurora PostgreSQL. Discover how to safeguard your data from unauthorized access, data breaches, and vulnerabilities.
Data Security Best Practices
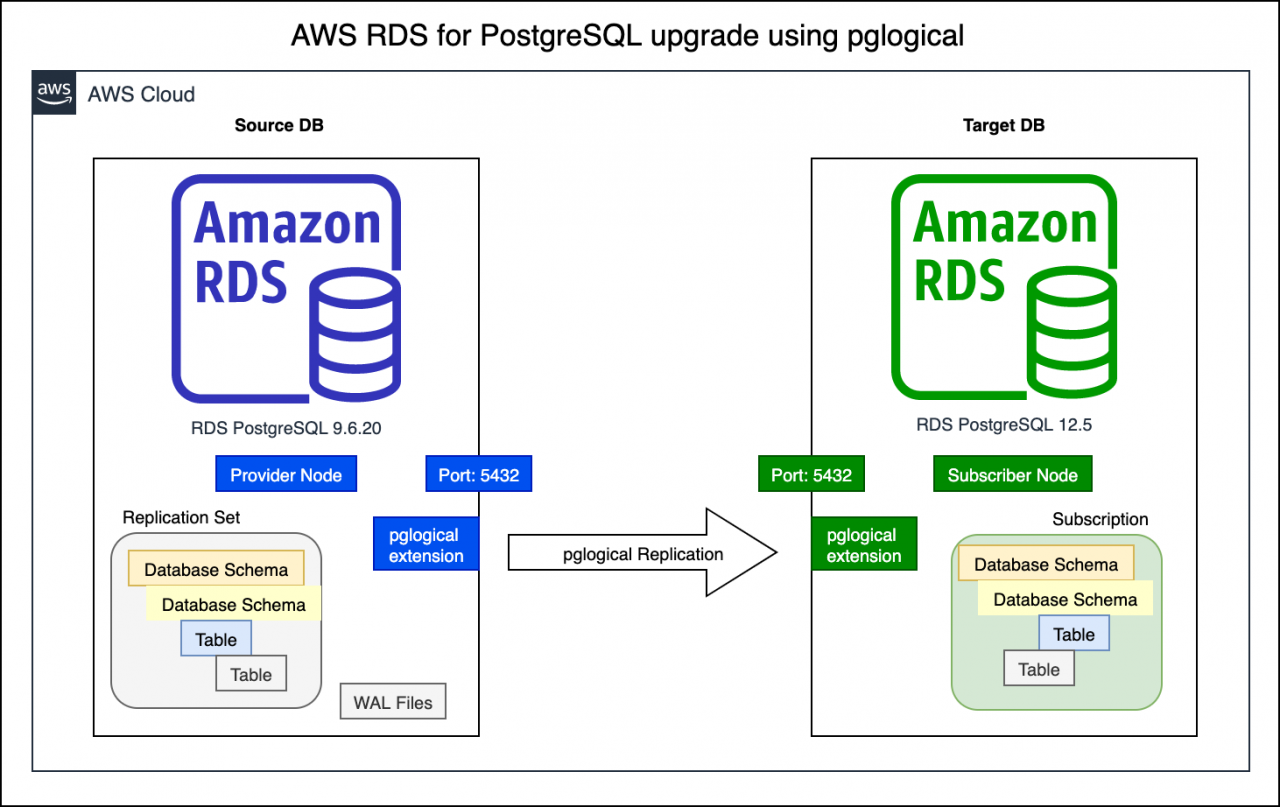
Data security is paramount for any organization that stores confidential data. A data breach can have devastating consequences, including financial losses, reputational damage, and legal liability. Therefore, it is essential to implement robust data security measures to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction.
Encryption, A company stores confidential data in an amazon aurora postgresql
Encryption is a critical data security best practice that involves converting plaintext data into an unreadable format, known as ciphertext. This makes it extremely difficult for unauthorized individuals to access or understand the data, even if they gain possession of it.
A company stores confidential data in an Amazon Aurora PostgreSQL database, which is a managed database service. The company is concerned about the security of its data, and is considering implementing additional security measures. One of the measures that the company is considering is using an Android phone to track the location of the database server.
This would allow the company to monitor the server’s location and ensure that it is not being accessed from unauthorized locations. To learn more about the possibility of tracking an iPhone with an Android phone, you can read this article: can a android phone track an iphone . After implementing this measure, the company can continue to store its confidential data in the Amazon Aurora PostgreSQL database with increased peace of mind.
There are various encryption algorithms available, each with its own strengths and weaknesses. Organizations should choose an encryption algorithm that is appropriate for their specific needs and risk tolerance.
A company stores confidential data in an Amazon Aurora PostgreSQL database. This database is highly secure and reliable, but it can be difficult to access from outside the company’s network. One way to access the database remotely is to use a VPN.
Another way is to use a third-party tool like can i listen to itunes on an android phone . These tools can provide a secure connection to the database and allow users to access their data from anywhere.
Amazon Aurora PostgreSQL Features
Amazon Aurora PostgreSQL is a managed, highly scalable, and reliable relational database service from Amazon Web Services (AWS). It combines the speed and reliability of PostgreSQL with the scalability and availability of AWS.
Aurora PostgreSQL offers a number of features that enhance data security, including:
- Encryption of data at rest and in transit
- Access control lists (ACLs) to restrict access to data
- Audit logging to track access to data
Aurora PostgreSQL is a good choice for businesses that need a highly scalable, reliable, and secure relational database service.
Comparison of Aurora PostgreSQL with Other PostgreSQL Options
Aurora PostgreSQL offers a number of advantages over other PostgreSQL options, including:
- Scalability:Aurora PostgreSQL can be scaled up or down to meet the needs of your application.
- Reliability:Aurora PostgreSQL is a highly reliable service, with a 99.99% uptime SLA.
- Security:Aurora PostgreSQL offers a number of features that enhance data security, including encryption of data at rest and in transit, access control lists (ACLs), and audit logging.
- Cost-effectiveness:Aurora PostgreSQL is a cost-effective service, with pricing that is based on usage.
If you are looking for a highly scalable, reliable, and secure relational database service, then Aurora PostgreSQL is a good option for you.
Data Encryption Options
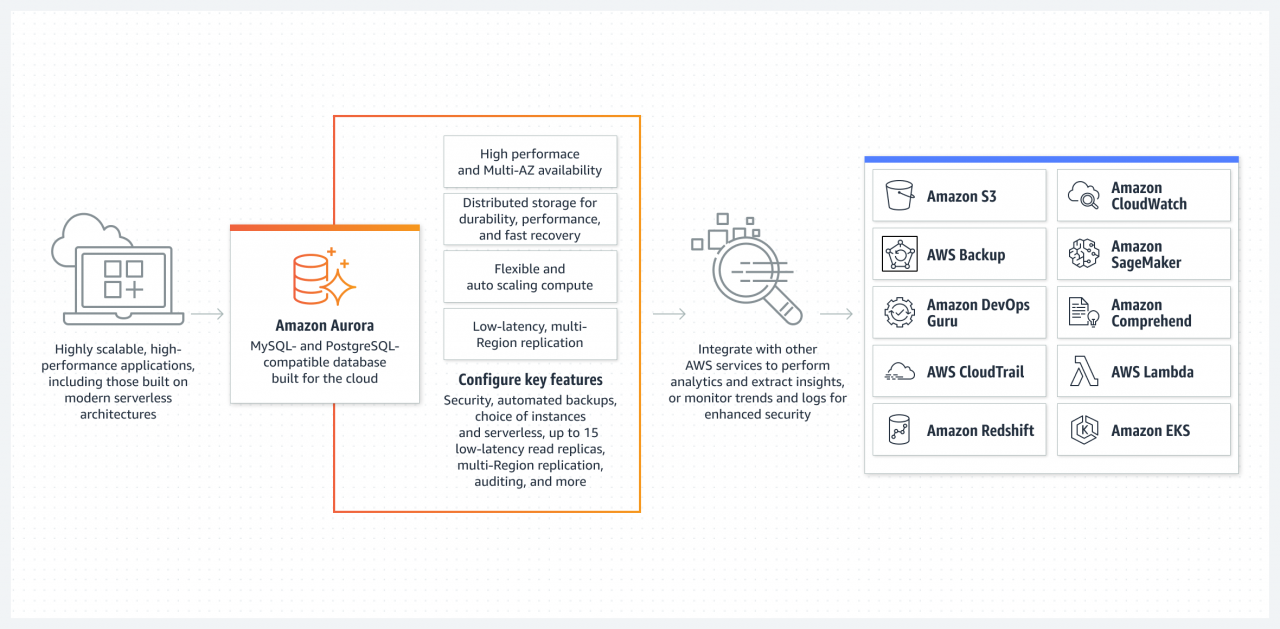
In Aurora PostgreSQL, you have a range of data encryption options to protect your confidential data. These options vary in their level of security, performance impact, and ease of use. Understanding the differences between these options will help you select the most appropriate encryption method for your specific needs.
Encryption at Rest
- Transparent Data Encryption (TDE): Encrypts data at rest on the storage layer. It is transparent to applications and requires no changes to the database schema or queries. TDE is highly secure but can impact performance.
- Row-Level Encryption (RLE): Encrypts individual rows or columns within a table. It provides finer-grained control over encryption but requires modifications to the database schema and can be more complex to implement.
Encryption in Transit
- SSL/TLS: Encrypts data in transit between the database and the client applications. It is essential for protecting data from eavesdropping on unsecured networks.
- IPsec: Encrypts data in transit between database instances or between the database and other services within a virtual private cloud (VPC).
Access Control and Authentication
Managing user access and authentication is crucial for data security. Aurora PostgreSQL offers robust access control mechanisms to ensure that only authorized users can access and modify data.
To safeguard sensitive data, many companies rely on Amazon Aurora PostgreSQL, a secure database service. Speaking of security, have you ever wondered if you can trade in your Android phone for an iPhone? Check it out here . Returning to the topic of data protection, Amazon Aurora PostgreSQL’s robust encryption and access controls ensure the confidentiality of stored data, providing peace of mind for businesses.
User Permissions and Roles
Aurora PostgreSQL uses a role-based access control system. Roles define a set of privileges that can be granted to users. Users can be assigned to multiple roles, allowing for granular control over permissions.
- CREATE ROLE:Creates a new role with a specified name.
- GRANT:Grants specific privileges to a role or user.
- REVOKE:Revokes privileges previously granted to a role or user.
Best Practices for Managing Database Access
To ensure secure database access, follow these best practices:
- Principle of Least Privilege:Grant only the minimum necessary permissions to users and roles.
- Regular Auditing:Regularly review user permissions and roles to identify any potential vulnerabilities.
- Use Strong Passwords:Enforce strong password policies to prevent unauthorized access.
- Monitor Access Logs:Monitor database access logs to detect suspicious activity.
Auditing and Monitoring
Monitoring and auditing are essential components of data security. Aurora PostgreSQL provides robust capabilities to track and log database activity, enabling you to detect and respond to security incidents promptly.
A company stores confidential data in an Amazon Aurora PostgreSQL database. To enhance security, they implement fine-grained access controls. However, employees using Android devices express concerns about accessing company data. To address this, the IT team explores if employees can access iCloud from an Android device.
This would allow them to access company data securely from their personal devices. The team evaluates the feasibility and security implications of this approach, ensuring compliance with company policies and industry best practices for data protection.
Aurora PostgreSQL offers comprehensive audit logging capabilities that can be configured to capture a wide range of events, including database logins, user activity, and database modifications. These logs provide a valuable source of information for security analysis and incident response.
Configuring Audit Logs and Alerts
Configuring audit logs and alerts is crucial for effective monitoring. Aurora PostgreSQL allows you to specify the types of events to be logged, the level of detail to be captured, and the destination of the logs.
Hey, did you know that a company stores confidential data in an Amazon Aurora PostgreSQL database? That’s some serious security! Speaking of security, can an AirTag be detected by an Android phone ? I’ve been wondering about that lately. Anyway, back to the company’s data: it’s encrypted and everything, so it’s super safe.
I mean, who would want to steal confidential data, right?
Alerts can be configured to notify you of specific events, such as failed login attempts or suspicious activity. These alerts can be sent via email, SMS, or other channels, ensuring that you are promptly notified of potential security incidents.
Interpreting Audit Data and Responding to Security Incidents
Interpreting audit data and responding to security incidents requires a systematic approach. By understanding the types of events logged and the context in which they occur, you can identify potential security risks and take appropriate action.
When a security incident occurs, it is important to follow a well-defined incident response plan. This plan should include steps for investigating the incident, containing the damage, and recovering from the attack.
Data Backup and Recovery
Data backup and recovery are critical aspects of data management, especially for confidential data stored in Amazon Aurora PostgreSQL. A robust backup and recovery plan ensures that data is protected against accidental deletion, hardware failures, or natural disasters, enabling businesses to restore data quickly and minimize downtime.
Aurora PostgreSQL offers several backup and recovery options, including automated backups, point-in-time recovery, and continuous backup. Automated backups are scheduled and managed by Aurora, providing peace of mind and reducing the risk of data loss. Point-in-time recovery allows users to restore data to a specific point in time, enabling them to recover from accidental deletions or data corruption.
A company stores confidential data in an Amazon Aurora PostgreSQL database, ensuring its security. But what if you’re wondering can I use Apple Pay with an Android phone ? The answer is no, but you can use other mobile payment options like Google Pay or Samsung Pay.
Returning to the topic, Amazon Aurora PostgreSQL provides robust data protection, so your confidential data remains safe.
Best Practices for Data Backup and Recovery
To ensure effective data backup and recovery, consider the following best practices:
- Establish a regular backup schedule and adhere to it.
- Store backups in a separate location from the primary database to prevent data loss in case of a disaster.
- Test the recovery process regularly to ensure that backups are reliable and data can be restored successfully.
- Educate users on the importance of data backup and recovery and their responsibilities in maintaining data integrity.
- Monitor backup logs and alerts to identify any potential issues and take prompt action.
Vulnerability Management
Storing confidential data in Aurora PostgreSQL introduces potential vulnerabilities that can compromise the integrity and security of the data. These vulnerabilities can arise from various sources, including software flaws, configuration errors, and malicious attacks. Identifying and mitigating these vulnerabilities is crucial for ensuring the protection of sensitive data.
Identifying Vulnerabilities
- Regular Security Audits:Conduct periodic security audits to identify potential vulnerabilities in Aurora PostgreSQL configurations, software versions, and access controls.
- Vulnerability Scanning:Use vulnerability scanning tools to detect known vulnerabilities in the Aurora PostgreSQL instance and its supporting infrastructure.
- Review Security Logs:Monitor security logs for suspicious activities or error messages that may indicate vulnerabilities.
Mitigating Vulnerabilities
- Apply Security Patches:Regularly apply security patches to the Aurora PostgreSQL instance and its underlying operating system to address known vulnerabilities.
- Configure Securely:Implement secure configurations for Aurora PostgreSQL, including strong passwords, access control lists, and encryption.
- Implement Intrusion Detection and Prevention Systems:Deploy intrusion detection and prevention systems to monitor network traffic for suspicious activities and prevent unauthorized access.
Keeping Aurora PostgreSQL Up-to-Date
Keeping Aurora PostgreSQL up-to-date with the latest security patches is essential for maintaining the integrity and security of confidential data. Here are some best practices:
- Regular Updates:Establish a regular schedule for applying security patches to the Aurora PostgreSQL instance and its supporting infrastructure.
- Test Patches:Before applying security patches, test them in a non-production environment to ensure compatibility and stability.
- Monitor for Updates:Subscribe to security bulletins and announcements from Amazon Web Services (AWS) to stay informed about the latest security patches for Aurora PostgreSQL.
Compliance and Regulatory Considerations
Aurora PostgreSQL adheres to various compliance and regulatory requirements, including industry standards, data protection laws, and regulations. Understanding these requirements is crucial for organizations storing confidential data in Aurora PostgreSQL.
Compliance Requirements
Organizations must identify the applicable compliance requirements based on their industry, location, and the nature of the data they store. Some common compliance requirements include:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- Sarbanes-Oxley Act (SOX)
- California Consumer Privacy Act (CCPA)
Configuring Aurora PostgreSQL for Compliance
Aurora PostgreSQL provides features and capabilities to help organizations meet compliance requirements. These include:
-
-*Encryption
Aurora PostgreSQL supports encryption at rest and in transit, ensuring data confidentiality.
-*Access Control
A company stores confidential data in an Amazon Aurora PostgreSQL database, which is a managed database service that provides high availability and scalability. However, some employees are asking if they can read Kindle books on an Android tablet. Can I read Kindle books on an Android tablet ? The answer is yes, you can read Kindle books on an Android tablet using the Kindle app.
The Kindle app is available for free on the Google Play Store. Once you have downloaded and installed the Kindle app, you can sign in with your Amazon account and start reading your Kindle books.
Role-based access control (RBAC) and fine-grained access controls allow organizations to restrict access to data based on user roles and permissions.
-*Auditing and Logging
Aurora PostgreSQL provides comprehensive auditing capabilities to track database activity and identify potential security breaches.
-*Data Backup and Recovery
Regular backups and point-in-time recovery capabilities ensure data integrity and availability in the event of data loss or corruption.
Certifications and Attestations
To demonstrate compliance, organizations may seek certifications and attestations from independent third parties. Aurora PostgreSQL has obtained certifications such as:
ISO 27001
2013
- SOC 2 Type II
- HIPAA Business Associate Agreement (BAA)
Obtaining these certifications provides assurance to customers that Aurora PostgreSQL meets industry-recognized security standards.
Incident Response Plan: A Company Stores Confidential Data In An Amazon Aurora Postgresql
An incident response plan is crucial for organizations storing confidential data in Amazon Aurora PostgreSQL. It Artikels a structured approach to handling security incidents, minimizing their impact and ensuring business continuity.The incident response process typically involves:
- Detection and identification of the incident
- Containment and isolation to prevent further spread
- Investigation to determine the root cause and scope
- Eradication of the threat or vulnerability
- Recovery and restoration of affected systems and data
- Post-incident analysis and improvement of security measures
Continuous Monitoring and Improvement

Continuous monitoring and improvement are crucial for maintaining a robust data security posture. Regularly assessing and evaluating security measures helps identify vulnerabilities, detect potential threats, and proactively address areas for enhancement. By leveraging metrics and analytics, organizations can gain insights into security performance, identify trends, and pinpoint areas where improvements can be made.
Establishing a Continuous Improvement Process
Implementing a continuous improvement process for data security involves:
- Establishing clear goals and objectives for data security.
- Defining metrics and analytics to measure progress towards these goals.
- Regularly monitoring and evaluating data security performance.
- Identifying areas for improvement based on data analysis.
- Implementing changes and enhancements to address identified vulnerabilities.
- Continuously reviewing and refining the improvement process to ensure ongoing effectiveness.
Concluding Remarks
By implementing the strategies Artikeld in this guide, you can effectively secure confidential data in Amazon Aurora PostgreSQL. Remember, data security is an ongoing process, and continuous monitoring and improvement are essential to maintain a robust defense against evolving threats.
Query Resolution
Is Aurora PostgreSQL more secure than regular PostgreSQL?
Yes, Aurora PostgreSQL offers additional security features, such as automatic backups, continuous monitoring, and enhanced encryption options.
How do I encrypt data in Aurora PostgreSQL?
You can use Transparent Data Encryption (TDE) or Column-level Encryption (CLE) to encrypt data at rest. TDE encrypts the entire database, while CLE allows you to encrypt specific columns.
How do I configure access control in Aurora PostgreSQL?
Aurora PostgreSQL supports role-based access control (RBAC), allowing you to assign specific permissions and roles to users and groups.