In today’s digital landscape, a web company is looking to implement an intrusion detection and prevention system to safeguard its critical assets and maintain a secure online presence. This comprehensive guide delves into the essential elements of intrusion detection and prevention, empowering web companies to proactively protect their systems and data from malicious attacks.
From understanding the fundamentals of IDPS to implementing best practices, this guide provides a roadmap for web companies to enhance their cybersecurity posture and stay ahead of evolving threats.
Company Profile
The web company specializes in providing comprehensive web solutions, including website design, development, and maintenance. The company has a team of experienced professionals who are passionate about creating innovative and user-friendly websites. The company has a proven track record of success in delivering high-quality websites that meet the needs of its clients.The
Yo, check it out! This fly web company is lookin’ to drop an intrusion that’ll be slicker than a whistle. But wait up, they wanna know if they can throw up a roadblock for a certain area code. Hold up, lemme check…
Yeah, I got you! You can totally block an area code on Android. Can I block an area code on Android . Bam! Now that’s sorted, let’s get back to that intrusion plan. Game on!
company is headquartered in the United States and serves a global clientele. The company’s target audience includes businesses of all sizes, from small startups to large corporations. The company is committed to providing its clients with the highest level of service and support.
Company Size, A web company is looking to implement an intrusion
The company has a team of over 50 experienced professionals. The company is growing rapidly and is always looking for talented individuals to join its team.
Industry
The company is a leader in the web development industry. The company has been recognized for its innovative work by a number of industry organizations.
Target Audience
The company’s target audience includes businesses of all sizes. The company has a proven track record of success in delivering high-quality websites that meet the needs of its clients.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are cybersecurity solutions designed to detect and respond to malicious activities within a network or system. They continuously monitor network traffic, analyze events, and take appropriate actions to protect against unauthorized access, data breaches, and other threats.
IDPSs work by identifying suspicious patterns and behaviors that deviate from normal network activity. When an anomaly is detected, the system can issue alerts, block suspicious traffic, or take other measures to mitigate the threat. This helps organizations to proactively identify and respond to potential security incidents before they cause significant damage.
A web company is looking to implement an intrusion detection system to protect its network from unauthorized access. They’re also wondering if they can read Kindle books on an Android tablet. Can I read Kindle books on an Android tablet ? The answer is yes, you can read Kindle books on an Android tablet using the Kindle app.
The Kindle app is available for free from the Google Play Store. Once you’ve downloaded and installed the Kindle app, you can sign in with your Amazon account and start reading your Kindle books. The Kindle app for Android has all the features you need to read Kindle books, including the ability to adjust the font size, brightness, and background color.
You can also create bookmarks, highlights, and notes. The Kindle app for Android is a great way to read Kindle books on your Android tablet.
Types of IDPS
There are two main types of IDPS:
- Network Intrusion Detection Systems (NIDS)monitor network traffic for suspicious patterns and behaviors. They are typically deployed at the network perimeter, such as firewalls or routers, and can detect threats such as malware, phishing attacks, and denial-of-service (DoS) attacks.
- Host Intrusion Detection Systems (HIDS)monitor individual hosts or endpoints for suspicious activities. They are installed on servers, workstations, and other devices and can detect threats such as unauthorized access, rootkit installations, and file integrity violations.
Each type of IDPS has its own advantages and disadvantages. NIDSs provide a broader view of network traffic and can detect threats that originate outside the organization. However, they can be more complex to deploy and manage. HIDSs provide more granular visibility into individual hosts and can detect threats that are specific to a particular system.
However, they can be more difficult to scale and may require more manual effort to manage.
Security Assessment
Conducting a security assessment involves evaluating an organization’s security posture to identify vulnerabilities and threats that could lead to intrusions. It’s a crucial process for organizations seeking to enhance their cybersecurity measures and mitigate potential risks.
A web company is looking to implement an intrusion detection system to protect its network from malicious attacks. However, the company is unsure if the system will be compatible with Android devices. Can someone with an Android use FaceTime ? This is a common question among Android users, as FaceTime is a popular video calling app that is exclusive to Apple devices.
While there are some third-party apps that allow Android users to make FaceTime calls, these apps often require both the caller and the recipient to have the app installed. This can be a major inconvenience, especially if the recipient does not have an Android device.
Fortunately, there is a way to use FaceTime on Android without having to install any third-party apps. By using a web-based FaceTime client, Android users can make FaceTime calls directly from their web browser. This makes it easy to stay connected with friends and family who have Apple devices, even if you don’t have an iPhone or iPad.
The company can use this method to test the compatibility of the intrusion detection system with Android devices.
Security assessments typically follow a structured approach that includes:
Planning and Preparation
- Define the scope and objectives of the assessment.
- Gather information about the organization’s IT infrastructure, applications, and data.
- Identify potential risks and vulnerabilities.
Vulnerability Scanning
- Use automated tools to scan the organization’s systems for known vulnerabilities.
- Identify vulnerabilities that could be exploited by attackers.
- Prioritize vulnerabilities based on their severity and risk.
Penetration Testing
- Simulate real-world attacks to test the effectiveness of the organization’s security controls.
- Identify weaknesses in the security posture that could be exploited by attackers.
- Provide recommendations for improving security.
Reporting and Remediation
- Document the findings of the security assessment in a comprehensive report.
- Prioritize the identified vulnerabilities and threats based on their risk.
- Develop and implement a remediation plan to address the identified vulnerabilities.
Intrusion Detection Methods
Intrusion detection systems (IDSs) employ various techniques to identify and respond to malicious activities. Two primary methods are signature-based detection and anomaly-based detection.
Signature-Based Detection
Signature-based detection matches incoming network traffic against a database of known attack signatures. These signatures are unique patterns or characteristics associated with specific attacks. When a match occurs, the IDS triggers an alert and takes appropriate actions.
Anomaly-Based Detection
Anomaly-based detection establishes a baseline of normal network behavior and identifies deviations from this baseline. It monitors traffic patterns, system behavior, and user activities to detect anomalies that may indicate malicious activity. Unlike signature-based detection, anomaly-based detection can identify novel or zero-day attacks that have not been previously encountered.
Intrusion Prevention Techniques
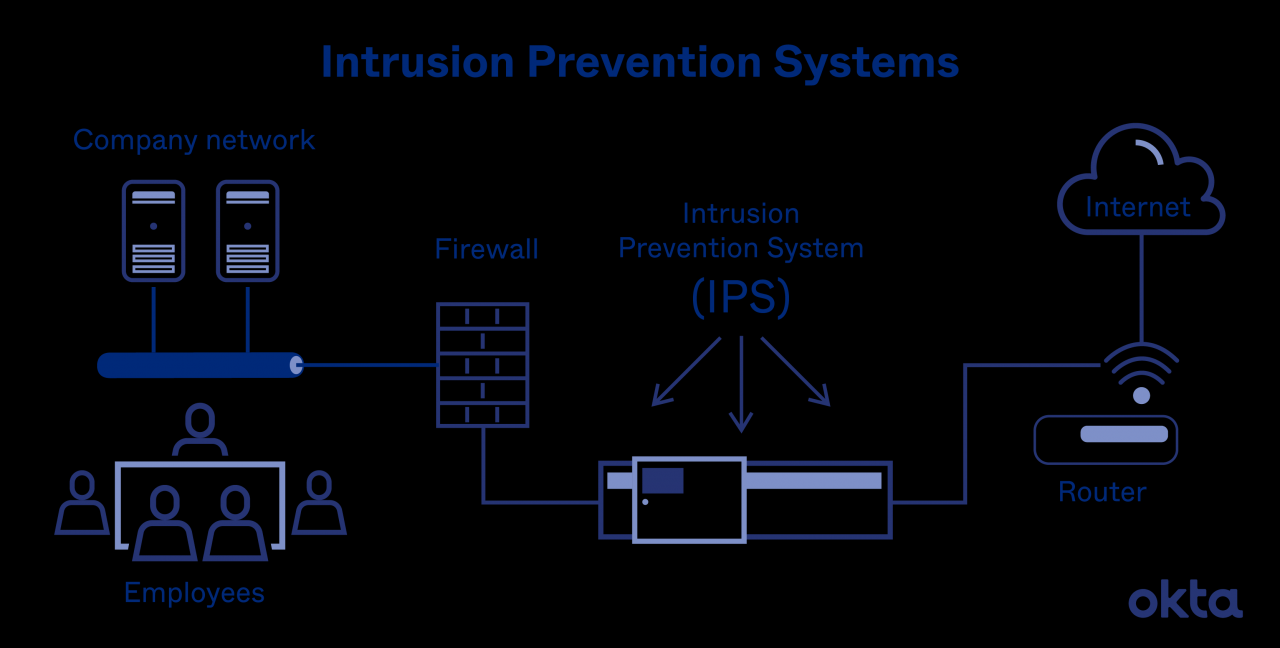
Intrusion prevention techniques are a critical part of any comprehensive security strategy. They can help to protect your systems from unauthorized access, data theft, and other malicious activity.
There are a variety of intrusion prevention techniques available, each with its own strengths and weaknesses. Some of the most common techniques include:
Signature-based intrusion detection
Signature-based intrusion detection systems (IDSs) look for specific patterns of activity that are associated with known attacks. When an IDS detects a signature, it can take action to block the attack, such as dropping the connection or sending an alert to the administrator.
Signature-based IDSs are relatively easy to deploy and manage, and they can be very effective at detecting known attacks. However, they can be less effective at detecting new or unknown attacks.
Anomaly-based intrusion detection
Anomaly-based intrusion detection systems (IDSs) look for deviations from normal behavior. When an IDS detects an anomaly, it can take action to block the activity or send an alert to the administrator.
Anomaly-based IDSs are more difficult to deploy and manage than signature-based IDSs, and they can be more prone to false positives. However, they can be more effective at detecting new or unknown attacks.
Network intrusion prevention systems (NIPS)
Network intrusion prevention systems (NIPSs) are devices that sit between the network and the host systems. They can inspect all traffic passing through the network and block any traffic that is malicious.
NIPSs are very effective at preventing attacks, but they can also be expensive and difficult to manage. They can also impact the performance of the network.
Host-based intrusion prevention systems (HIPS)
Host-based intrusion prevention systems (HIPSs) are software programs that run on individual host systems. They can monitor the activity of the system and block any activity that is malicious.
HIPSs are less expensive and easier to manage than NIPSs, but they can also be less effective. They can also impact the performance of the system.
Incident Response Plan
An incident response plan is a set of procedures that Artikels the steps to be taken in the event of a security breach or other incident. It is essential to have a plan in place so that organizations can respond quickly and effectively to incidents, minimizing damage and downtime.
The following are the steps involved in creating an incident response plan:
- Identify the potential risks and threats to the organization.
- Develop a plan for responding to each type of incident.
- Train staff on the incident response plan.
- Test the incident response plan regularly.
- Review and update the incident response plan as needed.
Having an incident response plan in place can help organizations to:
- Reduce the impact of security breaches and other incidents.
- Minimize downtime.
- Protect the organization’s reputation.
- Meet regulatory compliance requirements.
Employee Training and Awareness
Employee training plays a crucial role in preventing intrusions by educating employees about cybersecurity risks and best practices. Effective training programs include:
-
-*Security Awareness Training
Provides employees with a foundational understanding of cybersecurity threats, vulnerabilities, and countermeasures.
-*Phishing Simulations
Test employees’ ability to identify and avoid phishing emails, which are a common entry point for intrusions.
-*Role-Specific Training
Yo, a web company’s like, totally looking to break into the big leagues. They’re like, “We’re gonna hack into everything!” But hold up, they’re not the only ones with that game plan. A big company is also churning out a ton of hackers.
So, it’s like, a battle royale out there. Who’s gonna reign supreme in the cyber realm?
Tailors training to specific roles and responsibilities, ensuring employees understand the security implications of their actions.
-*Regular Updates
Keeps employees informed about emerging threats and best practices, ensuring their knowledge remains current.
Importance of Employee Training
-
-*Empowered Employees
Training empowers employees to recognize and respond to security threats, reducing the likelihood of successful intrusions.
-*Improved Security Posture
A well-trained workforce reduces the organization’s overall security risk by preventing breaches and minimizing the impact of incidents.
-*Compliance with Regulations
Many industries have regulations requiring organizations to provide cybersecurity training to employees.
Compliance and Regulations
Maintaining compliance with relevant standards and regulations is crucial for web companies implementing intrusion detection and prevention systems (IDPS).
Adherence to these standards ensures the company’s alignment with industry best practices, minimizes legal risks, and fosters trust among customers and stakeholders.
Relevant Standards and Regulations
- ISO 27001/27002:International standards for information security management systems, providing a framework for implementing and maintaining an effective IDPS.
- PCI DSS (Payment Card Industry Data Security Standard):Specifically designed for businesses handling credit card data, PCI DSS Artikels requirements for IDPS to protect sensitive information.
- GDPR (General Data Protection Regulation):An EU regulation that mandates companies to protect personal data, including measures like intrusion detection and prevention.
Best Practices for Intrusion Prevention
Implementing effective intrusion prevention measures is crucial for safeguarding networks and systems from malicious actors. By adhering to industry best practices and leveraging proven techniques, organizations can significantly reduce the risk of unauthorized access and data breaches.
One of the most effective intrusion prevention strategies is the deployment of Intrusion Detection and Prevention Systems (IDPS). These systems continuously monitor network traffic and analyze it for suspicious activities. When an anomaly or threat is detected, the IDPS can automatically take actions to block or mitigate the attack.
Security Assessment
Regular security assessments are essential for identifying vulnerabilities and weaknesses in an organization’s network infrastructure. These assessments involve thorough scans and evaluations of systems, networks, and applications to detect potential entry points for attackers.
A web company is looking to implement an intrusion detection system to protect its network from cyberattacks. The company has been experiencing an increase in suspicious activity on its network and wants to take steps to prevent any potential breaches.
The company has recently received an additional $500 investment from a venture capitalist, which will be used to fund the implementation of the intrusion detection system.
- Network Vulnerability Scanning: Scans the network for open ports, misconfigurations, and outdated software that could provide attackers with an entry point.
- Penetration Testing: Simulates real-world attacks to identify exploitable vulnerabilities and assess the effectiveness of existing security measures.
- Security Audits: Comprehensive reviews of an organization’s security policies, procedures, and controls to ensure compliance with industry standards and best practices.
Intrusion Detection Methods
Intrusion detection methods analyze network traffic and system activity to identify suspicious patterns or anomalies that may indicate an intrusion attempt. These methods include:
- Signature-Based Detection: Compares network traffic to known attack signatures to identify malicious activity.
- Anomaly-Based Detection: Detects deviations from normal network behavior, such as unusual traffic patterns or access attempts from unauthorized locations.
- Heuristic-Based Detection: Uses a combination of signature-based and anomaly-based techniques to identify novel or unknown attacks.
Intrusion Prevention Techniques
Intrusion prevention techniques actively block or mitigate intrusion attempts once they have been detected. These techniques include:
- Packet Filtering: Blocks network traffic based on specific criteria, such as source or destination IP addresses, ports, or protocols.
- Stateful Inspection: Analyzes the state of network connections to identify and block malicious traffic.
- Intrusion Prevention Systems (IPS): Implement a range of techniques, including packet filtering, stateful inspection, and anomaly detection, to prevent intrusions.
Incident Response Plan
An incident response plan Artikels the steps to be taken in the event of a security breach or intrusion attempt. This plan should include:
- Clear roles and responsibilities for incident response.
- Procedures for containment, eradication, and recovery.
- Communication protocols for internal and external stakeholders.
Employee Training and Awareness
Employees are often the first line of defense against intrusions. By providing regular training and awareness programs, organizations can educate employees on security best practices and empower them to identify and report suspicious activities.
A web company is looking to implement an intrusion and wants to gather data on Android devices. This can be a difficult task, but there are many resources available online that can help. For example, can i track an android phone from an iphone provides detailed instructions on how to track an Android phone from an iPhone.
By following these instructions, a web company can gather the data they need to implement an intrusion.
Compliance and Regulations
Organizations must comply with industry regulations and standards related to intrusion prevention. These regulations include:
- Payment Card Industry Data Security Standard (PCI DSS)
- Health Insurance Portability and Accountability Act (HIPAA)
- General Data Protection Regulation (GDPR)
Emerging Threats and Trends: A Web Company Is Looking To Implement An Intrusion
The landscape of intrusion detection and prevention is constantly evolving, with new threats and trends emerging all the time. It is important for organizations to stay up-to-date with the latest developments in order to protect themselves from these threats.
One of the most significant trends in recent years has been the rise of cloud computing. Cloud-based services offer many benefits, but they also introduce new security risks. Organizations need to be aware of these risks and take steps to mitigate them.
Another emerging trend is the increasing use of artificial intelligence (AI) in intrusion detection and prevention systems. AI can be used to identify patterns and anomalies in network traffic that may indicate an attack. AI-powered systems can also be used to automate the response to attacks, making it faster and more effective.
Staying Up-to-Date
It is important for organizations to stay up-to-date with the latest developments in intrusion detection and prevention. This can be done by:
- Reading industry publications
- Attending conferences and webinars
- Working with security vendors
Implementation Considerations
When implementing an Intrusion Detection and Prevention System (IDPS), it’s crucial to consider several factors to ensure a successful and effective deployment. These factors include cost, resources, and technical requirements.
The cost of an IDPS can vary depending on the size and complexity of the network, the features required, and the vendor selected. It’s important to factor in the cost of hardware, software, installation, maintenance, and ongoing support.
A web company is looking to implement an intrusion that will allow them to gain access to sensitive data. However, they are unsure if they can get Apple TV on an Android phone. If they can, it would open up a whole new avenue for them to attack.
Can I get Apple TV on an Android phone ? It’s a question that has been asked by many people, and the answer is yes, you can. There are a few different ways to do it, but the most popular method is to use a third-party app.
Once they have figured out how to get Apple TV on an Android phone, they can start planning their intrusion.
Resources
Implementing an IDPS requires dedicated resources, including personnel with the necessary skills and expertise to manage and maintain the system. This may include security analysts, network administrators, and IT support staff.
Technical Requirements
The technical requirements for an IDPS include hardware that meets the performance and capacity demands of the network, as well as software that is compatible with the operating system and network infrastructure. Additionally, the network infrastructure must be configured to support the IDPS, including the deployment of sensors and the establishment of communication channels.
Final Review
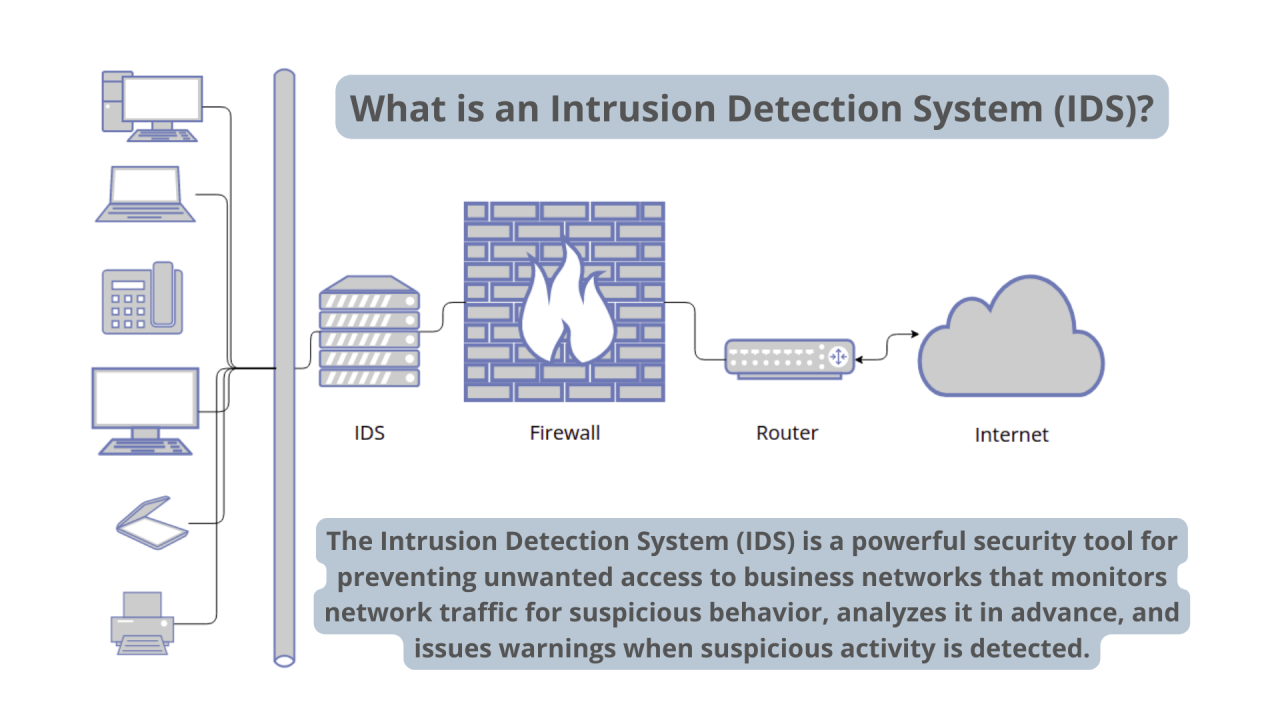
Implementing an effective intrusion detection and prevention system is crucial for web companies seeking to protect their digital assets and maintain a strong security posture. By embracing the strategies Artikeld in this guide, web companies can proactively mitigate risks, ensure business continuity, and foster trust among their customers and stakeholders.
FAQ Overview
What are the key components of an intrusion detection and prevention system?
An intrusion detection and prevention system typically comprises sensors, a central management console, and security policies. Sensors monitor network traffic and system activity for suspicious patterns, while the central console analyzes data and triggers alerts or takes preventive actions based on predefined policies.
How can web companies choose the right intrusion detection and prevention system for their needs?
When selecting an intrusion detection and prevention system, web companies should consider factors such as the size and complexity of their network, the nature of their business, and their specific security requirements. They should also evaluate the system’s features, performance, scalability, and ease of management.
What are the best practices for implementing an intrusion detection and prevention system?
Best practices for implementing an intrusion detection and prevention system include conducting a thorough security assessment, defining clear security policies, deploying sensors strategically, monitoring and analyzing data regularly, and implementing an incident response plan.